Azure log in: 5 Ultimate Tips for a Seamless Azure Log In Experience
Logging into Azure doesn’t have to be a headache. Whether you’re a developer, IT admin, or business user, mastering the azure log in process is your first step toward unlocking Microsoft’s powerful cloud ecosystem. Let’s make it smooth, secure, and simple.
Understanding Azure Log In: The Gateway to Cloud Power
The azure log in process is more than just entering a username and password—it’s your secure entry point to a vast suite of cloud services, including virtual machines, databases, AI tools, and enterprise applications. Microsoft Azure powers millions of businesses worldwide, and access begins with a reliable, secure login.
What Is Azure Log In?
Azure log in refers to the authentication process that allows users to access the Microsoft Azure portal, Azure Active Directory (Azure AD), and associated cloud resources. This login is typically managed through Microsoft accounts or organizational work/school accounts tied to Azure AD.
- It authenticates identity before granting access to cloud resources.
- Supports multiple user types: individual, enterprise, and guest accounts.
- Can be accessed via portal.azure.com, the primary entry point.
“Authentication is the cornerstone of cloud security—your azure log in is the first line of defense.” — Microsoft Security Best Practices
Why Azure Log In Matters for Businesses
In today’s hybrid and remote work environments, secure and efficient access to cloud infrastructure is non-negotiable. A poorly managed azure log in system can lead to security breaches, downtime, or compliance violations.
- Ensures only authorized personnel access sensitive data.
- Enables role-based access control (RBAC) for granular permissions.
- Integrates with identity management systems like Single Sign-On (SSO).
Step-by-Step Guide to Azure Log In
Navigating the azure log in process correctly ensures you gain immediate access without hiccups. Whether you’re logging in for the first time or troubleshooting an issue, this guide walks you through every stage.
How to Perform a Basic Azure Log In
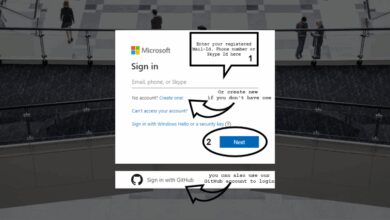
To log in to Azure, follow these simple steps:
- Open your preferred web browser and go to https://portal.azure.com.
- Enter your email address (typically your work or school account).
- Click “Next” and input your password.
- If enabled, complete multi-factor authentication (MFA).
- Upon successful verification, you’ll be redirected to the Azure dashboard.
This straightforward azure log in process works for most users, but additional configurations may apply depending on your organization’s security policies.
Using Microsoft Authenticator for Secure Access
For enhanced security, Microsoft recommends using the Microsoft Authenticator app during the azure log in process. This app generates time-based codes and supports push notifications for MFA.
- Download the app from the official Microsoft page.
- Link it to your Azure account via the Security Info page in My Account.
- Approve login requests directly from your mobile device.
“Over 99.9% of account compromises can be prevented by enabling MFA.” — Microsoft Digital Defense Report
Logging In with Guest Accounts (B2B Collaboration)
Azure supports external collaboration through Azure AD B2B, allowing guest users to perform an azure log in to access shared resources.
- Guests receive an email invitation with a link to sign in.
- They must use a Microsoft account or a work/school account from their own organization.
- Once accepted, they appear in the directory as guest users with limited permissions.
This feature is ideal for contractors, partners, or consultants who need temporary access without full onboarding.
Common Azure Log In Issues and How to Fix Them
Even the most experienced users encounter problems during the azure log in process. From forgotten passwords to MFA failures, knowing how to troubleshoot these issues saves time and frustration.
Forgot Password? Here’s What to Do
One of the most frequent azure log in issues is a forgotten password. Fortunately, Microsoft provides a self-service password reset (SSPR) tool.
- On the login screen, click “Forgot password?”
- Verify your identity using a registered phone number, email, or authenticator app.
- Set a new strong password following organizational guidelines.
If SSPR isn’t configured, contact your Azure administrator for assistance.
Multi-Factor Authentication (MFA) Problems
MFA is critical for security but can cause login failures if not set up correctly.
- App not receiving notifications: Check internet connectivity and ensure the Microsoft Authenticator app is updated.
- Lost or replaced device: Use backup methods like SMS or call verification, or contact your admin to reset MFA settings.
- Phishing attacks mimicking MFA: Never approve unexpected login prompts—report them immediately.
Organizations should educate users on recognizing legitimate MFA requests versus social engineering attempts.
Account Locked or Disabled
Sometimes, repeated failed attempts or policy violations result in an account being locked or disabled during the azure log in process.
- Wait for the lockout period to expire (usually 30 minutes).
- Contact your Azure AD administrator to unlock or re-enable the account.
- Review sign-in logs in Azure AD to identify suspicious activity.
Proactive monitoring through Azure Monitor or Microsoft Defender for Identity helps detect anomalies early.
Enhancing Security During Azure Log In
Security should never be an afterthought. As cyber threats evolve, so must your approach to the azure log in process. Implementing advanced security measures protects your data and maintains compliance.
Enable Multi-Factor Authentication (MFA)
MFA adds an extra layer of protection by requiring two or more verification methods:
- Something you know (password)
- Something you have (phone or token)
- Something you are (biometrics)
Admins can enforce MFA via Conditional Access policies in Azure AD. Learn more at Microsoft’s MFA documentation.
Use Conditional Access Policies
Conditional Access allows organizations to control when and how users perform an azure log in based on specific conditions.
- Block access from untrusted locations or devices.
- Require compliant devices (e.g., Intune-managed) for login.
- Enforce MFA for high-risk sign-ins detected by Identity Protection.
These policies are configured under Azure Active Directory > Security > Conditional Access.
“Conditional Access is the gatekeeper of modern identity security.” — Microsoft Azure Documentation
Leverage Identity Protection and Risk-Based Sign-Ins
Azure AD Identity Protection uses machine learning to detect risky sign-ins and user behavior.
- Identifies anomalies like sign-ins from unfamiliar locations.
- Flags leaked credentials found on the dark web.
- Automatically blocks or challenges high-risk logins.
Admins can set up risk policies to respond to threats in real time, reducing the attack surface during the azure log in phase.
Single Sign-On (SSO) and Azure Log In Integration
For enterprises managing multiple applications, Single Sign-On (SSO) streamlines the azure log in experience while improving security and user productivity.
What Is SSO and How Does It Work with Azure?
Single Sign-On allows users to log in once and gain access to multiple applications without re-entering credentials. Azure AD acts as an identity provider (IdP) for SSO integration.
- Users log in to Azure AD once and access connected apps like Office 365, Salesforce, or custom enterprise software.
- SSO supports protocols like SAML, OAuth, and OpenID Connect.
- Reduces password fatigue and phishing risks.
Explore available apps in the Azure AD Enterprise Applications gallery at Microsoft Learn.
Setting Up SSO for Custom Applications
Organizations often need to integrate internal or third-party apps with Azure for seamless logins.
- Navigate to Azure Portal > Azure Active Directory > Enterprise Applications.
- Click “New Application” and select “Non-gallery application” if not listed.
- Configure SSO settings using SAML or password-based methods.
- Upload metadata or configure URLs provided by the app vendor.
- Assign users or groups with appropriate roles.
Testing the azure log in flow post-configuration ensures compatibility and usability.
Benefits of SSO for Enterprise Users
Implementing SSO through Azure offers numerous advantages:
- Improved User Experience: No need to remember multiple passwords.
- Stronger Security: Centralized authentication reduces weak password usage.
- Easier Compliance: Audit trails and access logs are consolidated in Azure AD.
- Reduced IT Overhead: Fewer password reset requests and faster onboarding.
Companies like Contoso and Fabrikam have reported up to 40% reduction in helpdesk tickets after SSO deployment.
Using Azure CLI and PowerShell for Non-Browser Log In
Not all azure log in scenarios happen through a web browser. Developers and system administrators often use command-line tools like Azure CLI and Azure PowerShell for automation and scripting.
Logging In with Azure CLI
The Azure Command-Line Interface (CLI) allows users to manage Azure resources from the terminal.
- Install Azure CLI from Microsoft’s official site.
- Run
az loginin your terminal. - A browser window will open prompting you to complete the azure log in process.
- After authentication, the CLI displays your subscriptions.
For headless environments (e.g., CI/CD pipelines), use service principals or managed identities instead of interactive login.
Authenticating with Azure PowerShell
Azure PowerShell provides cmdlets for managing Azure services using PowerShell scripts.
- Install the Az module:
Install-Module -Name Az. - Run
Connect-AzAccountto initiate the azure log in. - Enter your credentials and complete MFA if required.
- Once authenticated, you can run commands like
Get-AzVMto list virtual machines.
Like CLI, PowerShell supports non-interactive authentication using service principals for automation.
“Automation starts with secure authentication—never hardcode credentials in scripts.” — Azure Best Practices Guide
Service Principals and Managed Identities
For applications and services that need to perform an azure log in without human interaction, service principals and managed identities are essential.
- Service Principal: A security identity used by apps, services, or automation tools to access Azure resources.
- Managed Identity: An automatically managed identity in Azure AD, eliminating the need to manage credentials.
These are crucial for securing backend processes, serverless functions, and infrastructure-as-code deployments.
Best Practices for a Smooth and Secure Azure Log In
To ensure reliability, performance, and security, follow these best practices every time you perform an azure log in or configure access for others.
Always Use Strong, Unique Passwords
A weak password undermines even the strongest security layers. Encourage users to create complex passwords with:
- At least 12 characters
- Mix of uppercase, lowercase, numbers, and symbols
- No personal information (e.g., names, birthdays)
Consider using a password manager to generate and store secure credentials.
Regularly Review Sign-In Logs
Azure AD provides detailed sign-in logs that help detect suspicious activity.
- Navigate to Azure AD > Monitoring > Sign-in logs.
- Filter by user, app, status, or risk level.
- Investigate failed logins or logins from unusual locations.
Set up alerts using Azure Monitor or Microsoft Sentinel for real-time threat detection.
Train Users on Phishing and Social Engineering
Even the most secure azure log in system can be compromised by human error. Regular training reduces the risk of credential theft.
- Educate employees on identifying fake login pages.
- Simulate phishing attacks to test awareness.
- Promote a culture of reporting suspicious emails or prompts.
Microsoft offers free security training resources at Microsoft Learn.
What if I can’t access my Azure account?
If you’re unable to log in to your Azure account, start by checking your internet connection and ensuring you’re using the correct email and password. Use the “Forgot password?” option to reset your credentials. If MFA is blocking access, try alternative verification methods. If issues persist, contact your Azure administrator or Microsoft Support for assistance.
Can I use personal Microsoft accounts for Azure log in?
Yes, personal Microsoft accounts (e.g., @outlook.com, @hotmail.com) can be used to sign up for free Azure trials or pay-as-you-go subscriptions. However, for enterprise use, organizations should use work or school accounts managed through Azure Active Directory for better control and security.
How do I enable MFA for my Azure account?
To enable MFA, go to the Microsoft 365 admin center or Azure portal, navigate to Azure Active Directory > Users > Multi-Factor Authentication. Select your user account and enable MFA. Alternatively, users can manage their own security info at https://mysignins.microsoft.com/security-info.
What is the difference between Azure AD and a regular Microsoft account?
Azure AD is an enterprise identity service designed for organizations, offering features like directory management, SSO, Conditional Access, and device registration. A regular Microsoft account is for individual consumers using services like Outlook, OneDrive, or Xbox. While both can be used for azure log in, Azure AD provides advanced administrative controls and security policies.
How can I automate Azure log in for scripts?
To automate azure log in in scripts, avoid interactive login methods. Instead, use service principals with client secrets or certificates, or leverage managed identities for Azure-hosted applications. These methods provide secure, non-interactive authentication suitable for CI/CD pipelines and automated workflows.
Mastering the azure log in process is essential for anyone using Microsoft’s cloud platform. From basic access to advanced security configurations, understanding how to log in securely and efficiently empowers users and protects organizational assets. By following best practices—like enabling MFA, using SSO, monitoring sign-ins, and leveraging automation—you ensure a robust and seamless experience. Whether you’re an admin, developer, or end-user, a well-managed azure log in is the foundation of cloud success.
Recommended for you 👇
Further Reading: