Sign In to Azure: 7 Ultimate Steps for Instant Access
Want to sign in to Azure but not sure where to start? You’re not alone. Millions of users log in daily to manage cloud resources, deploy apps, and secure data. This guide breaks down everything you need to know—step by step.
Sign In to Azure: The Complete Beginner’s Guide
Microsoft Azure is one of the world’s leading cloud platforms, powering businesses, developers, and IT professionals across the globe. Whether you’re managing virtual machines, deploying AI models, or securing enterprise data, the first step is always the same: sign in to Azure. But with multiple account types, authentication methods, and access levels, the login process can seem overwhelming at first.
Understanding how to sign in to Azure properly ensures you gain secure and efficient access to your cloud environment. This guide will walk you through every aspect of the login process, from basic steps to advanced troubleshooting, so you can navigate the Azure portal with confidence.
What Is Azure and Why Signing In Matters
Azure is Microsoft’s cloud computing platform, offering over 200 services including compute, storage, networking, analytics, and AI. To use any of these services, you must authenticate your identity by signing in. This authentication verifies who you are and determines what resources you can access.
Signing in to Azure isn’t just about logging into a dashboard—it’s the gateway to your entire cloud infrastructure. Whether you’re an administrator, developer, or end-user, your login experience shapes your productivity, security posture, and access control.
- Azure supports identity management via Microsoft Entra ID (formerly Azure Active Directory).
- Authentication is required for all Azure services, including the portal, CLI, PowerShell, and APIs.
- Incorrect sign-in attempts can trigger security alerts or account lockouts.
“Access begins with authentication. In Azure, signing in is the first line of defense and the foundation of cloud control.” — Microsoft Cloud Security Whitepaper
Types of Azure Accounts You Can Sign In With
Not all Azure accounts are the same. Depending on your role and organization, you might use different types of credentials to sign in. Here are the most common:
- Work or School Account: Provided by your organization through Microsoft Entra ID. This is the most common for enterprise users.
- Microsoft Account (MSA): A personal account like outlook.com, hotmail.com, or live.com. Often used for individual subscriptions.
- Guest User Account: Used when invited to another organization’s Azure environment via B2B collaboration.
- Service Principal: A non-human identity used by applications or automation tools to sign in programmatically.
Each account type has different permissions and authentication flows. For example, a work account might require multi-factor authentication (MFA), while a personal Microsoft account may not.
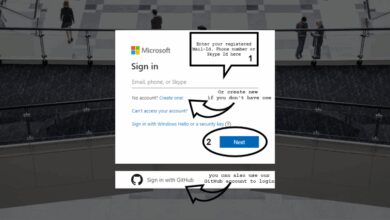
Step-by-Step: How to Sign In to Azure Portal
The Azure portal (portal.azure.com) is the primary web interface for managing cloud resources. Signing in is straightforward, but knowing the nuances can save time and prevent errors.
Navigate to the Official Azure Sign-In Page
The first step is to go to the correct URL: https://portal.azure.com. Always ensure you’re on the official Microsoft domain to avoid phishing scams.
Once loaded, you’ll see a clean login screen prompting for your email, phone, or Skype username. This is your Microsoft account or work/school email associated with Azure.
- Never use third-party links claiming to be Azure login pages.
- Bookmark the official portal for future access.
- Use HTTPS—check for the padlock icon in your browser.
Enter Your Credentials and Authenticate
After entering your email, click ‘Next’. You’ll be prompted to enter your password. If your account has multi-factor authentication (MFA) enabled, you’ll need to complete an additional verification step.
sign in to azure – Sign in to azure menjadi aspek penting yang dibahas di sini.
MFA methods include:
- Microsoft Authenticator app notification or code
- Text message (SMS) with a one-time passcode
- Phone call verification
- Security key (FIDO2 compliant)
Once authenticated, you’ll be redirected to the Azure dashboard, where you can view your subscriptions, resource groups, and services.
“Over 99.9% of account compromises could be prevented with multi-factor authentication.” — Microsoft Security Report 2023
Common Sign-In Errors and How to Fix Them
Even with the right credentials, you might encounter errors when trying to sign in to Azure. Here are the most frequent issues and their solutions:
“We can’t sign you in with this credential because your organization requires use of a device that’s joined to your corporate network or has a work or school account.” This means conditional access policies are enforced.Ensure your device is compliant or use a registered corporate device.”Your sign-in was blocked.Contact your admin.” This could be due to suspicious activity or policy violations..
Contact your Azure administrator to review sign-in logs.”The user account [email] does not exist in the [directory] directory.” You may be signing in to the wrong tenant.Use the ‘Sign in to a different account’ option or switch directories.Password expired or needs reset.Follow the password reset link or contact your IT department.Microsoft provides a detailed troubleshooting guide for sign-in problems, including real-time diagnostics via the Azure portal..
Sign In to Azure Using CLI and PowerShell
For developers and DevOps engineers, interacting with Azure via command-line tools is often more efficient than using the portal. Both Azure CLI and Azure PowerShell allow you to sign in to Azure from your terminal.
How to Sign In to Azure CLI
The Azure Command-Line Interface (CLI) is a cross-platform tool for managing Azure resources. To sign in:
- Install Azure CLI from https://learn.microsoft.com/en-us/cli/azure/install-azure-cli
- Open your terminal (Command Prompt, PowerShell, or Bash)
- Run the command:
az login
This opens a browser window where you can sign in with your credentials. Once authenticated, the CLI displays your subscriptions.
If you have multiple accounts, specify a tenant with:
az login --tenant <tenant-id>
For automation, use service principals with client secrets or certificates.
Signing In with Azure PowerShell
Azure PowerShell is a module that lets you manage Azure through PowerShell cmdlets. To get started:
sign in to azure – Sign in to azure menjadi aspek penting yang dibahas di sini.
- Install the Az module:
Install-Module -Name Az - Run:
Connect-AzAccount
You’ll be prompted to sign in via a web browser. After successful authentication, you can list your subscriptions with Get-AzSubscription.
- Use
Connect-AzAccount -Tenant <tenant-id>to target a specific directory. - For headless scripts, use service principal authentication.
“Automation starts with authentication. Secure sign-in methods are critical for CI/CD pipelines and infrastructure-as-code workflows.” — Azure DevOps Documentation
Managing Multiple Subscriptions After Signing In
Once signed in, you might have access to multiple Azure subscriptions. Use the following commands to manage them:
- Azure CLI:
az account listto view all subscriptions. Set the active one withaz account set --subscription <subscription-id> - Azure PowerShell:
Get-AzSubscriptionandSelect-AzSubscription -SubscriptionId <id>
Always verify your active subscription before deploying resources to avoid billing or permission issues.
Secure Your Sign In to Azure with MFA and Conditional Access
Security is paramount when accessing cloud environments. A simple password is no longer enough. Microsoft recommends enabling multi-factor authentication (MFA) and conditional access policies to protect your Azure sign-in process.
Enabling Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring a second form of verification. To enable MFA:
- Sign in to the Azure portal as an administrator.
- Navigate to Microsoft Entra ID > Protection > Multifactor Authentication.
- Select users and enable MFA for them.
Users will be prompted to set up their second factor on next sign-in. Options include the Microsoft Authenticator app, phone calls, or hardware tokens.
- MFA reduces the risk of account takeover by over 99%.
- It’s required for all global administrators by Microsoft’s security defaults.
Configuring Conditional Access Policies
Conditional Access (CA) allows you to enforce rules based on user, device, location, and risk level. For example, you can block sign-ins from untrusted locations or require compliant devices.
To create a CA policy:
- Go to Microsoft Entra ID > Protection > Conditional Access.
- Click New policy.
- Define conditions (e.g., user group, cloud app = Azure Management).
- Set access controls (e.g., require MFA, device compliance).
- Enable the policy and assign it.
Example policy: “Require MFA for all users accessing Azure from outside the corporate network.”
“Conditional Access is the cornerstone of Zero Trust security in Azure.” — Microsoft Identity Best Practices
Using Identity Protection to Detect Risky Sign-Ins
Azure Identity Protection monitors sign-in attempts and detects anomalies like impossible travel, unfamiliar locations, or leaked credentials.
It assigns a risk score to each sign-in and can automatically enforce actions like blocking access or requiring password resets.
sign in to azure – Sign in to azure menjadi aspek penting yang dibahas di sini.
- Access Identity Protection via Microsoft Entra ID > Protection > Identity Protection.
- Review risky sign-ins and user risks regularly.
- Integrate with Azure Monitor and Sentinel for advanced threat detection.
For organizations with Azure AD Premium P2 licenses, Identity Protection provides real-time alerts and automated remediation.
Sign In to Azure with Single Sign-On (SSO) and Federation
For enterprises with existing identity systems, Azure supports federated authentication and single sign-on (SSO), allowing users to sign in using their on-premises credentials.
How SSO Works with Azure AD
Single Sign-On enables users to access multiple applications—including Azure—with one set of credentials. When you sign in to Azure, the request is redirected to your identity provider (IdP), such as Active Directory Federation Services (AD FS) or third-party IdPs like Okta or PingIdentity.
Benefits of SSO:
- Reduced password fatigue
- Centralized identity management
- Improved security through centralized policies
SSO can be configured via Password Hash Sync, Pass-Through Authentication, or Federation with AD FS.
Setting Up Federation with AD FS
To federate your on-premises Active Directory with Azure:
- Deploy AD FS servers in your network.
- Configure a relying party trust for Azure AD.
- Run the
Convert-MsolDomainToFederatedPowerShell cmdlet.
After federation, users signing in to Azure will be redirected to your AD FS login page instead of the Microsoft login screen.
This method is ideal for organizations that want full control over authentication and session management.
“Federation bridges the gap between on-premises identity and cloud access, ensuring seamless and secure sign-ins.” — Microsoft Hybrid Identity Guide
Using SAML and OAuth for Application SSO
Azure supports industry-standard protocols like SAML 2.0 and OAuth 2.0 for application-level SSO. When users sign in to Azure, they can automatically access integrated apps like Salesforce, Dropbox, or custom enterprise applications.
To configure SAML-based SSO:
- Register the application in Azure AD.
- Upload the IdP metadata or configure manually with entity ID, reply URL, and certificates.
- Assign users or groups.
For OAuth, use Azure AD as an authorization server to grant secure access tokens to applications.
sign in to azure – Sign in to azure menjadi aspek penting yang dibahas di sini.
Advanced: Sign In to Azure Using Service Principals and Managed Identities
For automated workflows, applications, and serverless functions, human login isn’t practical. Azure provides non-interactive authentication methods: service principals and managed identities.
Creating and Using a Service Principal
A service principal is an identity created for an application to sign in to Azure programmatically.
To create one:
- Sign in to Azure CLI or PowerShell.
- Run:
az ad sp create-for-rbac --name "MyAppSP"
This returns a client ID, client secret, and tenant ID. Use these credentials in your app to authenticate.
Best practices:
- Assign the principle the least privilege necessary (e.g., Contributor, Reader).
- Rotate secrets regularly.
- Use certificates instead of secrets when possible.
What Are Managed Identities and How They Work
Managed identities eliminate the need to manage credentials altogether. Azure automatically creates and manages an identity for your resource (e.g., VM, App Service).
There are two types:
- System-assigned: Tied to the lifecycle of a specific resource.
- User-assigned: Standalone identity that can be assigned to multiple resources.
To enable a system-assigned identity on a VM:
- Go to the VM in the Azure portal.
- Navigate to Identity > System assigned > On.
- Save. Azure creates an identity in Microsoft Entra ID.
Your application can then request an access token from the Azure Instance Metadata Service (IMDS) to call other Azure services securely.
“Managed identities remove the burden of secret management and reduce the attack surface.” — Azure Security Benchmark
Comparing Service Principals vs. Managed Identities
Both allow non-interactive sign-ins, but they serve different use cases:
| Feature | Service Principal | Managed Identity |
|---|---|---|
| Credential Management | Manual (secrets/certs) | Automatic by Azure |
| Lifecycle | Independent of resources | Tied to resource (system-assigned) |
| Use Case | CI/CD pipelines, local scripts | VMs, App Services, Functions |
| Security | Requires secret rotation | No secrets to manage |
For most cloud-native applications, managed identities are the recommended approach.
sign in to azure – Sign in to azure menjadi aspek penting yang dibahas di sini.
Troubleshooting: What to Do When You Can’t Sign In to Azure
Even with best practices, sign-in issues happen. Here’s a systematic approach to diagnosing and resolving them.
Check Your Internet Connection and Browser Compatibility
Before diving into complex fixes, ensure basic connectivity:
- Test your internet connection.
- Use a supported browser: Chrome, Edge, Firefox, or Safari.
- Clear cache and cookies or try incognito mode.
- Disable browser extensions that might interfere (e.g., ad blockers).
Sometimes, a simple browser refresh or restart resolves the issue.
Verify Account Status and Permissions
If you’re locked out, check:
- Is your account enabled? (Contact admin if disabled)
- Has your password expired?
- Are you using the correct tenant? (Switch directories in the portal)
- Do you have a valid Azure subscription?
Use the Microsoft account activity page to see recent sign-in attempts.
Use Azure Sign-In Logs for Diagnostics
Azure provides detailed sign-in logs in Microsoft Entra ID. To access them:
- Sign in as an administrator.
- Go to Microsoft Entra ID > Monitoring > Sign-in logs.
You can filter by:
- User
- Application
- Sign-in status (success/failure)
- IP address
- Device
Look for error codes like:
- 50076: MFA required
- 50140: Password change required
- 53000: Device not compliant
These logs are essential for auditing and forensic analysis.
“90% of security incidents involve identity. Monitoring sign-in logs is non-negotiable.” — Microsoft Digital Defense Report
Best Practices for a Smooth and Secure Sign In to Azure
To ensure a reliable and secure login experience, follow these proven best practices.
Always Use Strong, Unique Passwords
Your password is the first line of defense. Use a password manager to generate and store complex passwords. Avoid reusing passwords across accounts.
sign in to azure – Sign in to azure menjadi aspek penting yang dibahas di sini.
- Minimum 12 characters
- Mix of uppercase, lowercase, numbers, and symbols
- No personal information (e.g., name, birthday)
Enable Security Defaults or Identity Protection
Microsoft offers Security Defaults—a built-in policy that enforces MFA for admins and blocks legacy authentication. It’s free and easy to enable.
For advanced protection, upgrade to Azure AD Premium P2 and use Identity Protection to detect and respond to risky sign-ins.
Regularly Review and Clean Up User Access
Unused or overprivileged accounts are security risks. Conduct regular access reviews:
- Remove inactive users.
- Revoke unnecessary permissions.
- Use Just-In-Time (JIT) access for admins.
Azure’s Access Reviews feature automates this process.
“Privilege escalation is a top attack vector. Regular access reviews mitigate this risk.” — NIST Cybersecurity Framework
How do I sign in to Azure if I forgot my password?
If you forget your password, go to the password reset page, enter your email, and follow the instructions. You’ll need access to a registered phone, email, or authenticator app to verify your identity.
Can I sign in to Azure without MFA?
Yes, if MFA is not enforced by your administrator. However, Microsoft strongly recommends enabling MFA for all users, especially administrators, to prevent unauthorized access.
What is the difference between a Microsoft account and a work account in Azure?
A Microsoft account (MSA) is a personal account (e.g., @outlook.com). A work account is managed by an organization via Microsoft Entra ID. Work accounts support advanced security policies like MFA and conditional access.
How do I switch between Azure directories after signing in?
sign in to azure – Sign in to azure menjadi aspek penting yang dibahas di sini.
In the Azure portal, click your profile icon in the top-right corner, then select ‘Switch directory’. Choose the tenant you want to access from the list.
Why am I getting a ‘No subscriptions found’ error after signing in?
This means your account doesn’t have access to any Azure subscriptions in the current directory. Contact your administrator to assign you to a subscription or switch to the correct tenant.
Signing in to Azure is more than just entering a username and password—it’s the foundation of your cloud security and operational efficiency. From basic portal access to advanced automation with service principals, every login method plays a critical role. By following best practices like enabling MFA, monitoring sign-in logs, and using managed identities, you can ensure secure and seamless access to your Azure environment. Whether you’re a beginner or an expert, mastering the sign-in process empowers you to unlock the full potential of Microsoft’s cloud platform.
Further Reading: